Technitium DNS Server
Help Topics
Contents
- Introduction
- Understanding The Dashboard
- How To Create A Zone
- How To Delegate A Zone
- How To Do Conditional Forwarding
- Configuring DNS Server Local Addresses
- Configuring SSL/TLS For Accessing DNS Server Web Console
- Configuring DNS-over-TLS And DNS-over-HTTPS Optional DNS Server Protocol
- Configuring Prefetching And Auto Prefetching Options
Note: The page will be updated to cover more topics in future. If you have any queries, do send an email to support@technitium.com.
1. Introduction
Technitium DNS Server is a free, open source, cross-platform, authoritative and recursive DNS server that is aimed at self hosting a local DNS Server for privacy and security, software development and testing on small to medium size networks. It works out-of-the-box with no or minimal configuration and provides a user friendly web console accessible using any web browser.
The server packs a lot of features that should be understood before making any configuration changes:
Cross-Platform: Built using .NET 5, the server can be installed on Windows, Linux, macOS and even on Raspberry Pi. The server would work on any platform that you can install .NET on.
Blocked Zones: Supports blocking any domain name either by adding them manually or by using one or more block list URLs. The server updates the blocked zone using the block list URLs every 24 hours automatically. Allowed zones allows to add exception to unblock domain names listed in blocked zones.
Authoritative: Allows you to create zones to host your domain name. The authoritative zone supports features like wildcard records, enabling or disabling individual records, zone delegation using NS records, etc.
Recursive: Allows you to recursively resolve any domain name using pre-configured root servers or using forwarders.
-
Caching: Caching allows the server to quickly respond to queries for which it had received a response earlier. The server caches DNS records and uses the record's TTL value to keep the record in cache for that many seconds. Thus, you will see the TTL value count down in every subsequent response. When the TTL value reaches 0, the record is considered expired or stale and the DNS server must refresh the record again. The server also supports advance caching features like serve stale, prefetching and auto prefetching.
The serve stale feature works automatically and keeps expired entries in cache for up to 3 days so that when the server is unable to resolve the domain name, the stale entry in cache is returned instead of failing to resolve the domain name. The idea behind this feature is that a stale bread is better than no bread. The server returns stale response if the domain's name servers are not responding or if the server is unable to reach forwarder servers or if there is any network connectivity issue.
When the server receives a query for which it has a valid records in cache, the server returns the cached records and checks if the record TTL is less than prefetch trigger. If the TTL value is indeed less than the trigger value, the prefetch feature will trigger a background task to refresh the record in cache. This allows frequently queried records from expiring so that the server can respond to queries with minimum delays.
In addition to prefetch feature which is dependent on receiving queries to check for trigger, the auto prefetch feature keeps eligible records refreshed in cache keeping the cache "hot" for popular queries to allow fast response times.
The server also does negative caching, that is if a domain name does not exists, the server will cache this response to avoid querying for same request again. The SOA minimum value from the response is used as a TTL value for such cache entries. Similarly, a server failure response will also get cached for minimum of 300 (5 minutes) to prevent constant querying to the authoritative name server.
DNS Apps: Just like web apps run on a web server, DNS apps run on the DNS server. The DNS server includes an Apps framework which allows you to create and install custom apps on the DNS Server. Using an APP record in your primary zone, you can specify which installed app should handle the DNS request. The response provided by the DNS app is then returned to the client. The DNS server also includes an DNS App Store which has built-in apps that can be installed and used.
DNS-over-TLS and DNS-over-HTTPS: The server supports these new optional secure protocols along with standard UDP/TCP port 53. These optional protocols provide privacy and security over network since the default UDP and TCP protocols are vulnerable to snooping and MiTM attacks.
-
Forwarders: Forwarders are other recursive DNS servers that you can configure so that your DNS server queries them instead of doing recursive resolution itself. This feature allows you to chain multiple recursive DNS servers.
Forwarders can be configured with DNS-over-UDP, DNS-over-TCP, DNS-over-TLS, or DNS-over-HTTPS protocol. Using forwarders, you can setup the DNS server to use any of the public DNS resolvers like Cloudflare, Google or Quad9.
-
Proxy: This DNS server is probably the only one that supports using HTTP or SOCKS5 proxy allowing you to route DNS traffic over any network. This feature is specifically useful when you want your DNS traffic to be routed via Tor network.
Combining proxy and forwarder feature, its possible to use Cloudflare's hidden DNS resolver hosted over .onion address. The advantage of such a setup is that you are effectively hiding all your DNS traffic from your ISP and from Tor exit nodes (since hidden services are end-to-end encrypted and data never exits Tor network) while also masking your IP address from Cloudflare. In addition to that, Tor keeps switching to different circuits every 10 minutes by default and thus, your hidden connection to Cloudflare too keeps changing making it difficult to co-relate with your previous session that was on different circuit.
IPv6 Support: The server has IPv6 support capabilities allowing you to host the server on native IPv6 networks. IPv6 support is disabled by default and should be enabled from Settings only if your server has native IPv6 connectivity. Enabling IPv6 support when you don't have native IPv6 connectivity will severely affect the server performance.
-
DHCP Server: The server includes a built-in DHCP Server that is intergrated internally with the DNS Server. The DHCP server allows creating multiple network scopes to allow working with multiple networks on the server or with relay agents. With DHCP domain name option configured, the server will automatically configure forward and reverse DNS records for all clients on the network.
Logging: The server supports optional query logging feature that will log query and response data into a daily log file. By default the server does error and audit logging.
Web Console: The server provides a built in web console that internally uses REST API calls to configure the server. It is possible to use these REST API calls directly from any application to configure the server or to develop a similar web console.
DNS Client: The web console has a built-in DNS Client interface that allows you to query any DNS server using any supported protocol. It also has an Import feature that can be used to import records in the response into a local authoritative zone.
The DNS Server is ideal for use by end users by directly installing it on each of their computers/laptops or installing it on a single computer and configuring the DHCP server for entire network usage. Latest secure protocols like DNS-over-TLS or DNS-over-HTTPS are not supported by most software applications or operating systems and thus, having Technitium DNS Server installed allows using public DNS resolvers like Cloudflare, Google or Quad9 with these secure protocols.
Recommended way to use the DNS server on a small/home network is to install the server on a Raspberry Pi 3 B+ single board computer and connect it directly to your Internet router. Such a setup allows device on your entire network to use secure protocol and also allows you a greater control over your network such as blocking domain names on your network as per your policy or blocking Ads on your entire network.
2. Understanding The Dashboard
Technitium DNS Server web console provides a dashboard which displays useful stats that can be used to understand the DNS server operations. The dashboard contains a main chart which displays query and response related data, and a couple of donut (pie) charts. It also lists top clients, top domains and top blocked domains in a tabular format.
Main Chart
The dashboard can display stats for last hour, last day, last week, last month, last year, and custom time frames. The server internally stores all stats with UTC time stamps but, the dashboard displays the time on x-axis of the main chart by converting it into local time.
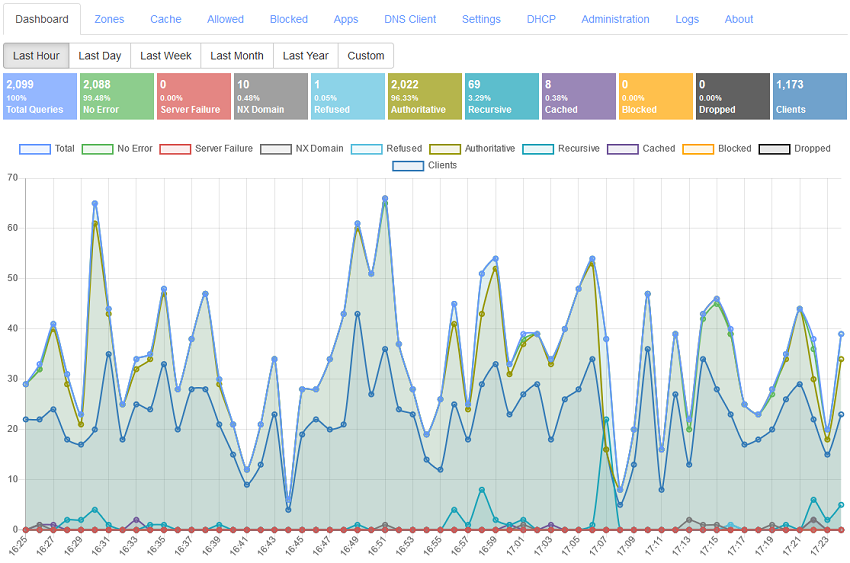
The stats displayed at the top of the main chart are also plotted on the chart using the same color scheme. Lets understand each item in the stats and chart:
Total Queries: These are the total number of queries the DNS server has received from all clients.
No Error: The total number of queries that were responded positively by the server. This usually means that the server was able to satisfy the query with desired response either from cache zone, authoritative zone, blocked zone, or by recursively resolving it.
Server Failure: This is an important stat to keep an eye on. It indicates total number of queries that the server failed to respond positively. This is a generic failure that can be caused by many different factors. Most common factor is network connectivity, that is, the server was unable to connect to the name server or forwarder server either due to Internet connectivity issues or due to the remote name server failing to respond within a time period usually of 2 seconds. Exact reason for failure can only be deduced from the logs.
NX Domain: The server will try to resolve a domain name in the query and if the domain name does not exists, it will receive a NX Domain response code which is also relayed as a response to the original query. NX Domain responses are generated only by authoritative name server of a domain name and recursive DNS servers only relay these responses. Too many NX Domain count can be a sign of malware infection since many malware designs use Domain Generation Algorithms (DGA) which are used to generate and register the domain name only when the malware controller loses access to primary domain name and thus you get NX Domain due to the generated domain names being unregistered. You should immediately check the computer that is generating too many NX Domain queries for malware infection.
Refused: The total number of queries this DNS server refused to resolve. This can commonly occur when you have "Allow Recursion Only For Private Networks" enabled in settings and the server receives a recursive query request from public network.
Authoritative: The total number of queries that were resolved from the zones hosted locally on the DNS server.
Recursive: The total number of queries that were resolved partially or fully resolved by recursive resolution.
Cached: The total number of queries that were resolved using data available in the server's cache. Higher cache percentage is better since, the DNS server did not need to resolve the query recursively and responded quickly from the cache.
Blocked: The total number of queries this DNS server blocked by responding with "0.0.0.0" (or "::" for AAAA) for A record request. The DNS server uses Blocked Zone, and Block List Zone (which can be configured with block list URLs in settings).
Clients: The total number of unique clients based on IP address of the queries.
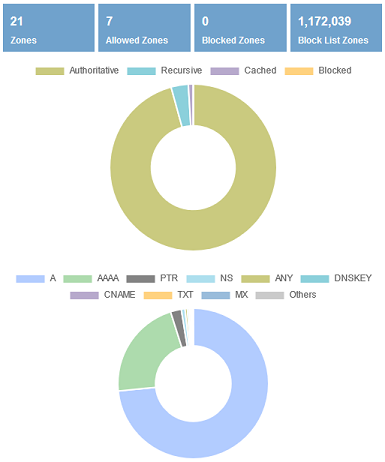
Donut Charts
These donut (pie) charts show the source of responses and the share of top 10 query types that this DNS server received for the selected time frame. Most common entry for query type chart is type A (which returns IPv4 address) and type AAAA (which returns IPv6 address). Although you don't have IPv6 connectivity, some applications like web browsers do query for an AAAA record to test IPv6 connectivity.
This section also includes stats for total Zones, Allowed Zones, Blocked Zones, and Block List Zones by the DNS server.
3. How To Create A Zone
You can create a zone for any domain name on the DNS server and the server will respond authoritatively to queries for these zones. This allows you to host domain names locally for development or testing purposes or even host your domain name live on the Internet. The server allows disabling zones such that when disabled, the server will perform resursive resolution for the domain name. This feature allows you to test your website or application in a local staging setup with same domain names used in production.
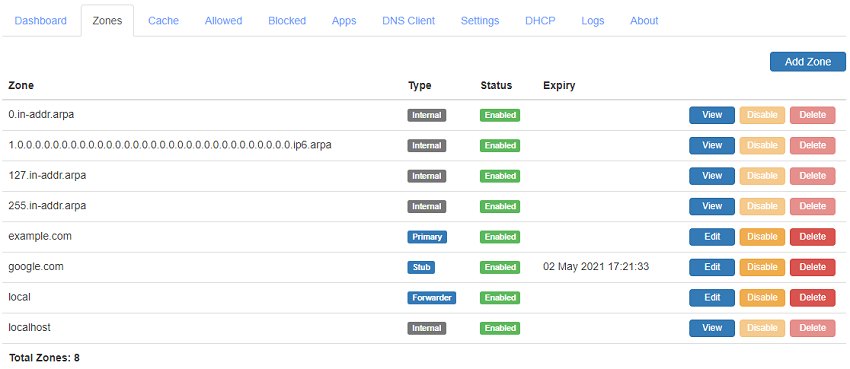
Use the Add Zone button to quickly create a zone. Use the Edit button to manage the zone records. The server also supports disabling individual records in a zone to allow you to switch between different servers that can be helpful during testing.
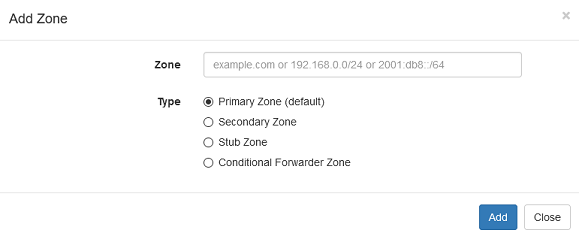
The DNS Server supports the following type of zones:
Primary: The primary zone allows hosting a authoritative zone on the DNS server.
Secondary: The secondary zone allows hosting a authoritative zone that is a copy of its primary zone on the DNS server. Secondary zones are automatically synced when there is any change made on the primary zone. They are used for redundancy and load balancing.
Stub: The stub zone allows the DNS server to keep track of the authoritative name servers for the zone. Having a stub zone will cause the DNS Server to perform recursive resolution for the zone even when a forwarder is configured in settings.
Conditional Forwarder: The conditional forwarder zone allows you to specify one or more specific forwarder servers to resolve the domain name. This zone also allows you to create records for the domain name to allow overriding the live zone.
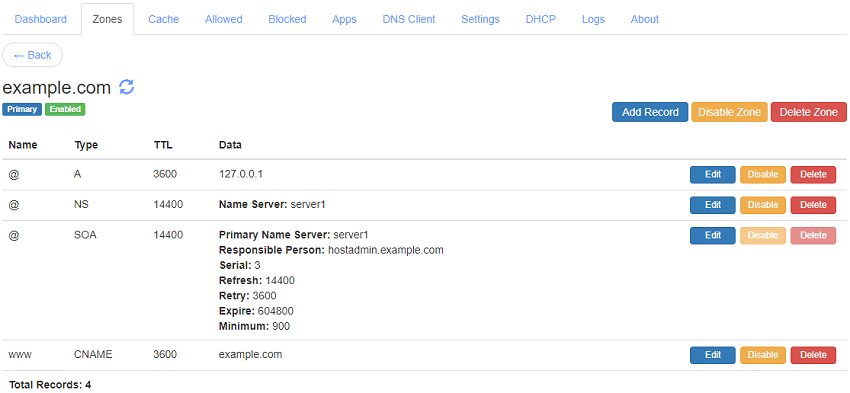
A DNS record consists of Name, Type, TTL, and Data. Name is the sub domain name or '@' which indicates no sub domain for the record. Records can be of different types based on the data they hold e.g. for adding an IP address Type A record is used. TTL is the time in seconds that other DNS resolvers should cache the record. When the TTL expires, the DNS resolvers must refresh the record again by doing a recursive resolution.
Following are the record types that you can add in your zone that are currently supported:
- A: Address record allows you to assign an IPv4 address to your domain or sub domain.
- NS: Name Server (NS) records tell other DNS resolvers the domain names of the authoritative DNS Servers that are hosting the current zone.
- SOA: There can be only one Start of Authority (SOA) record for a zone. The SOA record contain settings that are required by secondary name servers or recursive resolvers to know the minimum TTL for caching non existent record.
- CNAME: Canonical name record allow you to point your domain or sub domain to another domain name.
- PTR: Pointer records allow you do map a domain name to an IP address to allow performing reverse lookups i.e. finding domain name associated with an IP address.
- MX: Mail Exchange (MX) records allow you specify email servers so that you can receive email for your domain.
- TXT: Text records allow specifying any text data. These records are commonly used for domain name verification process and for Sender Policy Framework (SPF) record to prevent your domain being misused for email spam.
- AAAA: This address record allows you to assign an IPv6 address to your domain or sub domain.
- SRV: Service record allow certain applications to discover where a service is hosted.
- CAA: Certification Authority Authorization (CAA) record allows you to specify which Certificate Authority is allowed to issue SSL/TLS certificates for your domain name to prevent misuse.
- ANAME: This record allows you to have a CNAME like facility at the zone's apex. It can also be used for a sub domain. The DNS Server resolves the provided domain name in the record and returns A or AAAA response as per the QTYPE.
- FWD: The FWD record allows you to specify the forwarder server address to be used in conditional forwarder zones.
- APP: The APP record allows you to specify which DNS App should be used to process the request.
4. How To Delegate A Zone
Zone delegation is used to allow hosting a sub domain as an independent zone on another DNS server. For example, if you own 'example.com' domain name, the 'com' zone is delegating 'example.com' zone to your current name servers. This is achieved by creating NS records for the sub domain.
If you are hosting 'example.com' zone on your DNS server and you wish to delegate 'internal.example.com' to another DNS server then you can create NS record with name "internal" and point to the domain name of the other DNS server.
You can similarly delegate your existing domain name hosted on another DNS server to your locally running DNS server. Note that for hosting any zone on Internet, you will need to have a static IP address assigned by your Internet provider.
5. How To Do Conditional Forwarding
Conditional forwarding is a feature that allows you to specify DNS server which should be queried for a given domain name. This feature is often useful when you are having an internal DNS server that hosts your Intranet domain names for your organization and you want Technitium DNS Server to query those internal DNS servers for all the internal domain names.
To configure your internal domain 'internal.example.com' with conditional forwarding, follow the steps below:
- Create 'internal.example.com' Conditional Forwarder zone and specify the address of the forwarding server and the protocol to use.
- Once the zone is created, you can add more FWD records for the same zone that use another forwarding server, or have a sub domain that uses a different forwarding server.
Once you complete these steps, Technitium DNS Server will query the internal DNS server for 'internal.example.com' zone.
6. Configuring DNS Server Local End Points
Technitium DNS Server by default listens for queries on all your network interfaces. This is done with the default configured with 0.0.0.0:53 (for IPv4 networks) and [::]:53 (for IPv6 networks) end points as "DNS Server Local End Points" in the Settings. If you wish that the DNS service should be only accessible for a particular network on your server, you can specify the IP address of that network interface and the DNS Server will listen for queries only on that network interface. Note that you will also need appropriate firewall configuration to prevent other networks from accessing the DNS server if the network is routable.